iSecurity GUI Release News
Audit
System Configurations: Added Monitor Activity of Jobs, System, JobQ and OutQ:
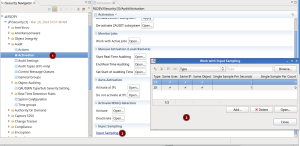
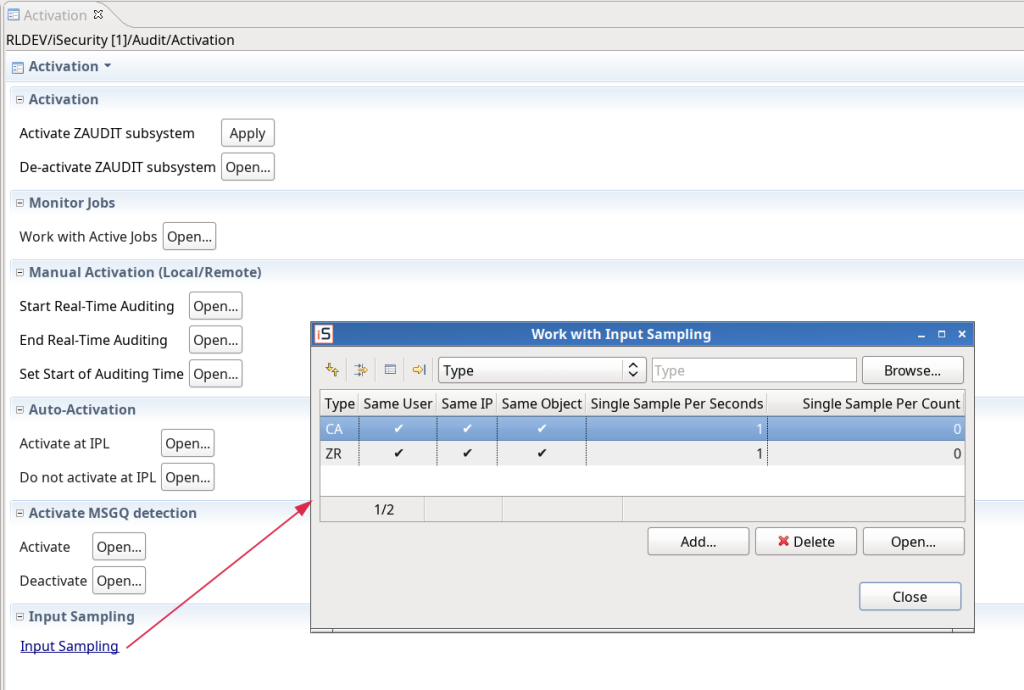
Input sampling: Added a link for the dialog
MFA
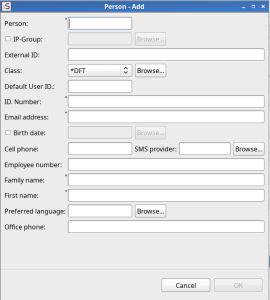
Persons: Adjusted to native.
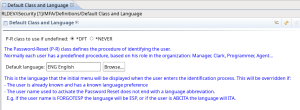
Added: Default Class and Language.
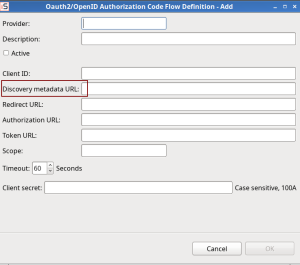
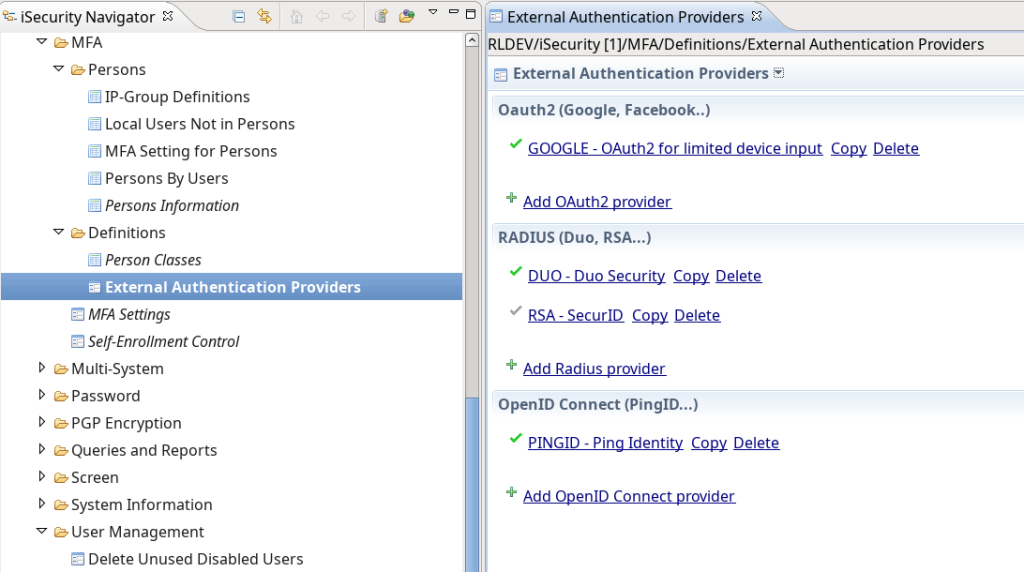
External Authority Providers:
- Updated: Metadata discovery URL for signature verification of JWTs in OpenID Connect and Oauth2.
- Fixed: a bug in secret encryption.
Firewall
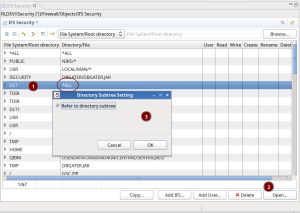
Adjusted: IFS Security in Firewall 19.03: Allow Open for directories that are *ALL
- GDPR (Encryption) discovery – count records: Optimization and bug fix
- Check authorization for Capture 5250: call SMZC/GSEPWDR instead of SMZ4/GSEPWDR.
- Firewall – User/group security -Servers: if all verbs of server are allowed and server is configure to ‘by verb’, the server is allowed too. (adjusted to native)
Dashboard
System info: added authorization code columns: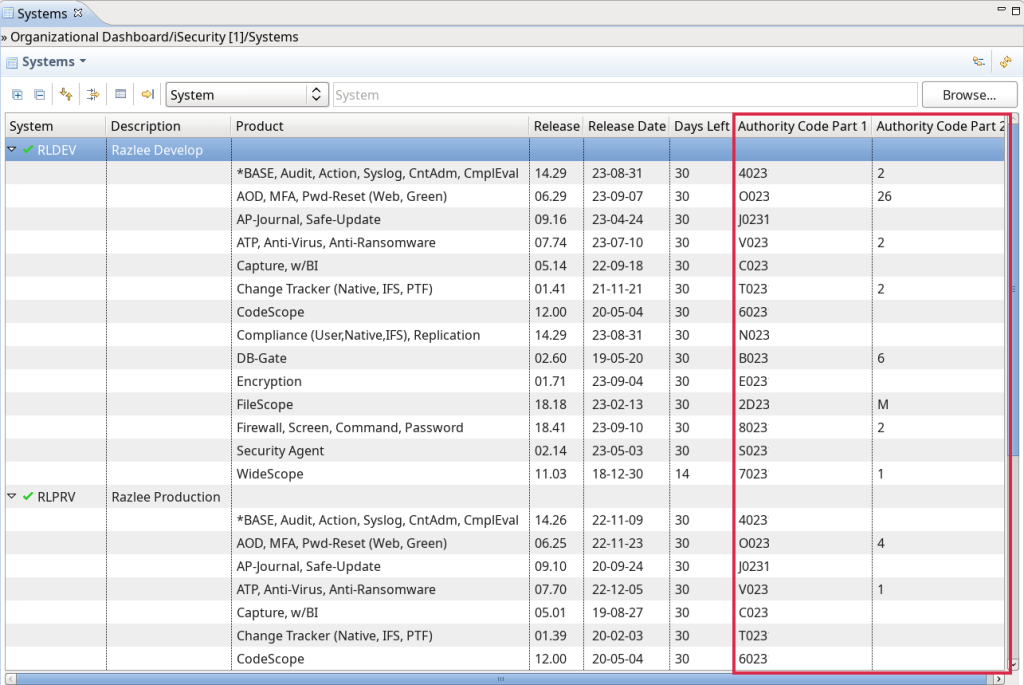
Installation of products:
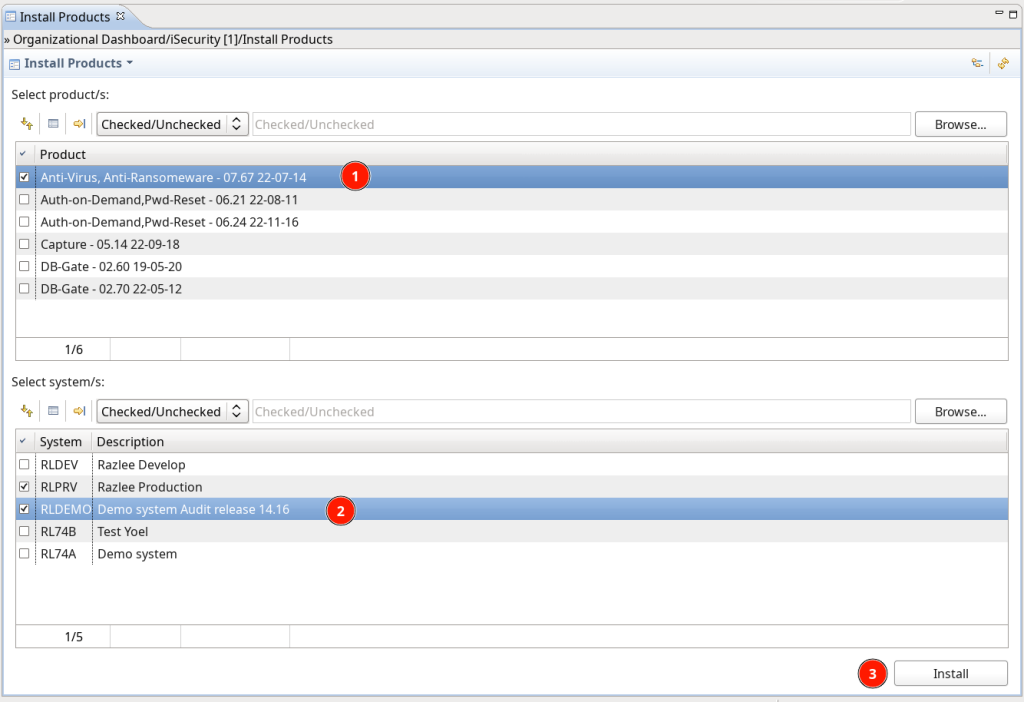
General
Help is now available from the IBM’s command prompter:
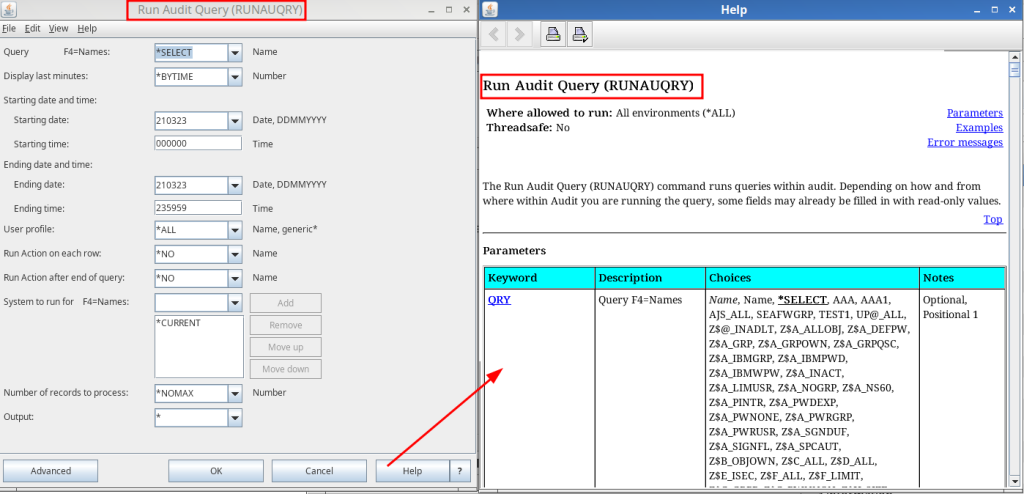
Audit
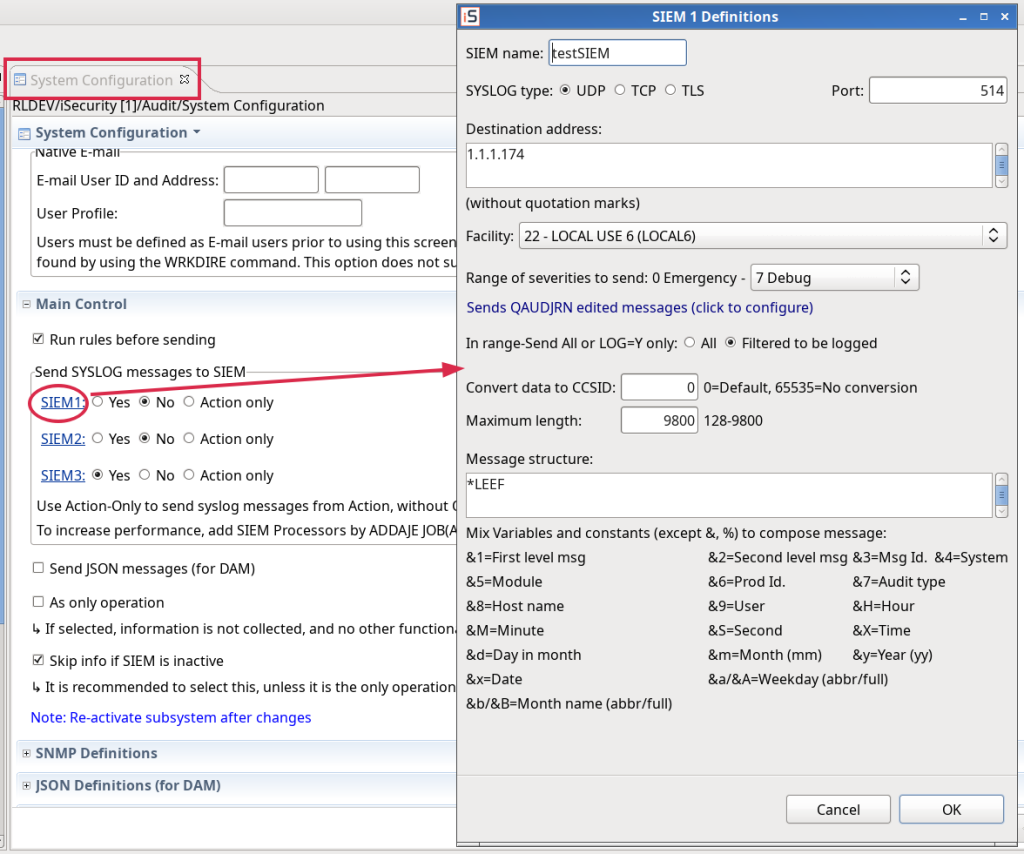
System configuration – SIEM: adjusted to native.
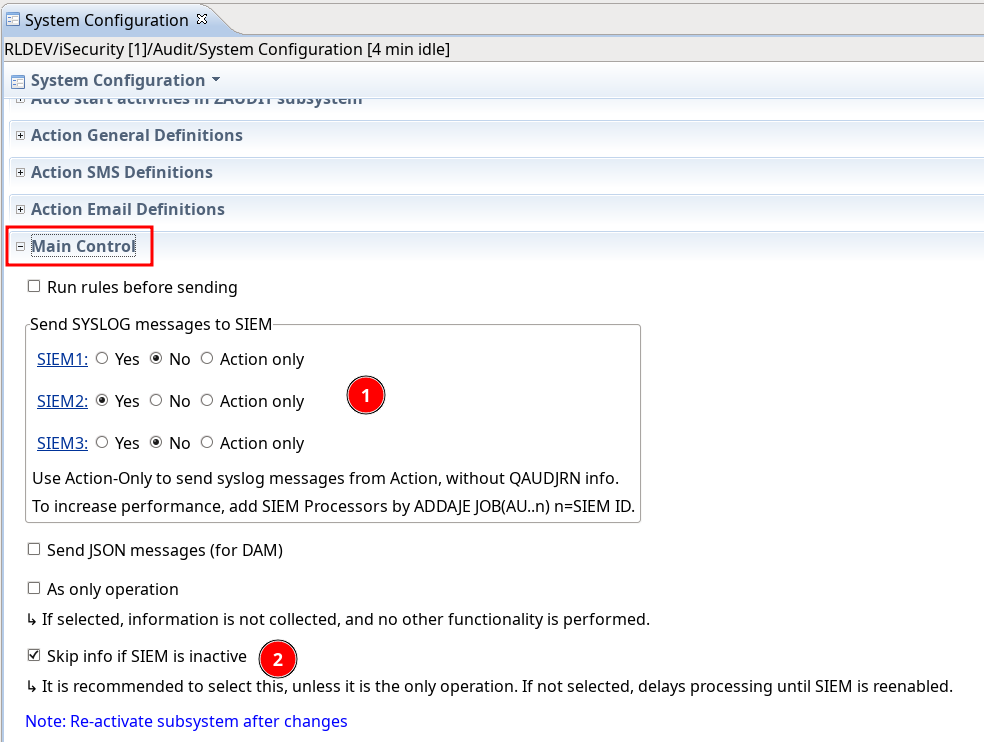
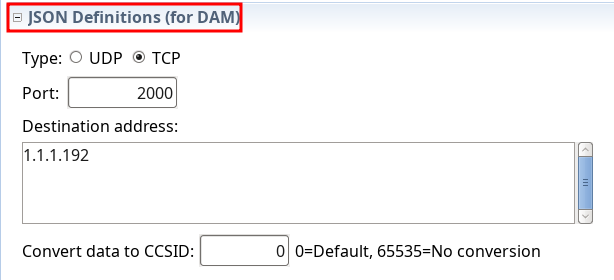
System configuration: removed Twitter settings and added JSON Definitions (for DAM)
QAUDJRN Severity Setting – SIEM: adjusted to native
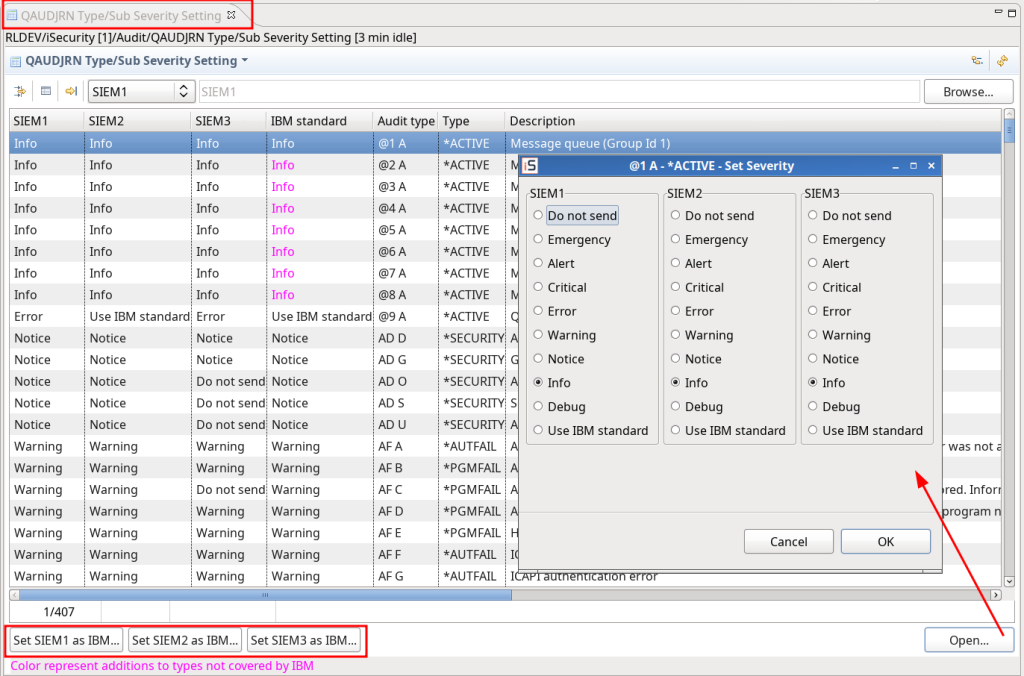
Input Sampling added:
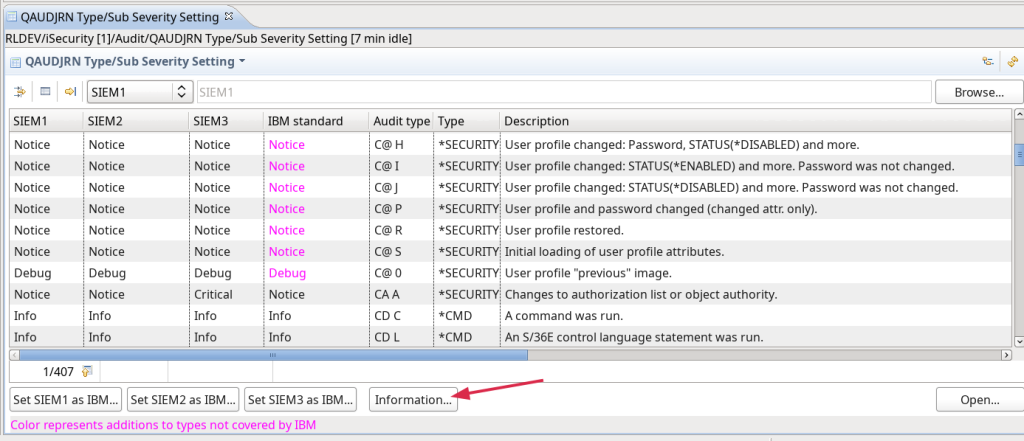
Added QUAUDJRN info button:
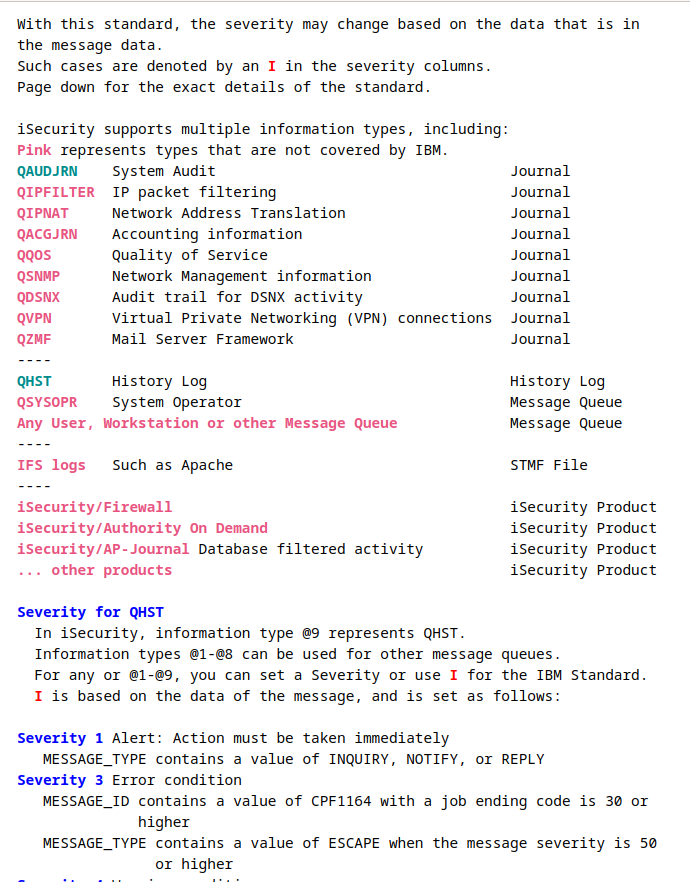
Information is displayed in the browser:
Firewall
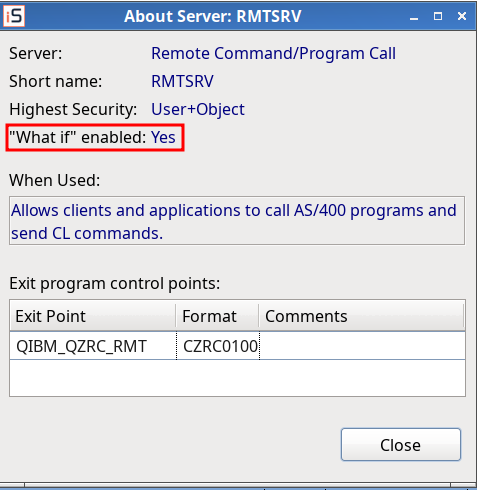
Server Settings – About Server: added “what if” status.
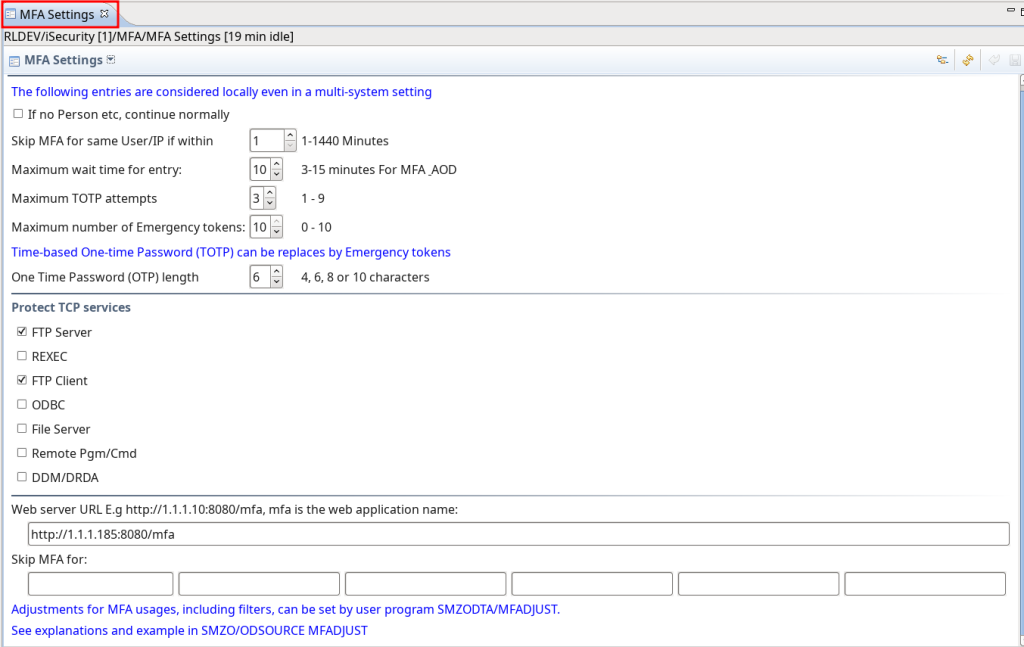
MFA
Settings adjusted to native
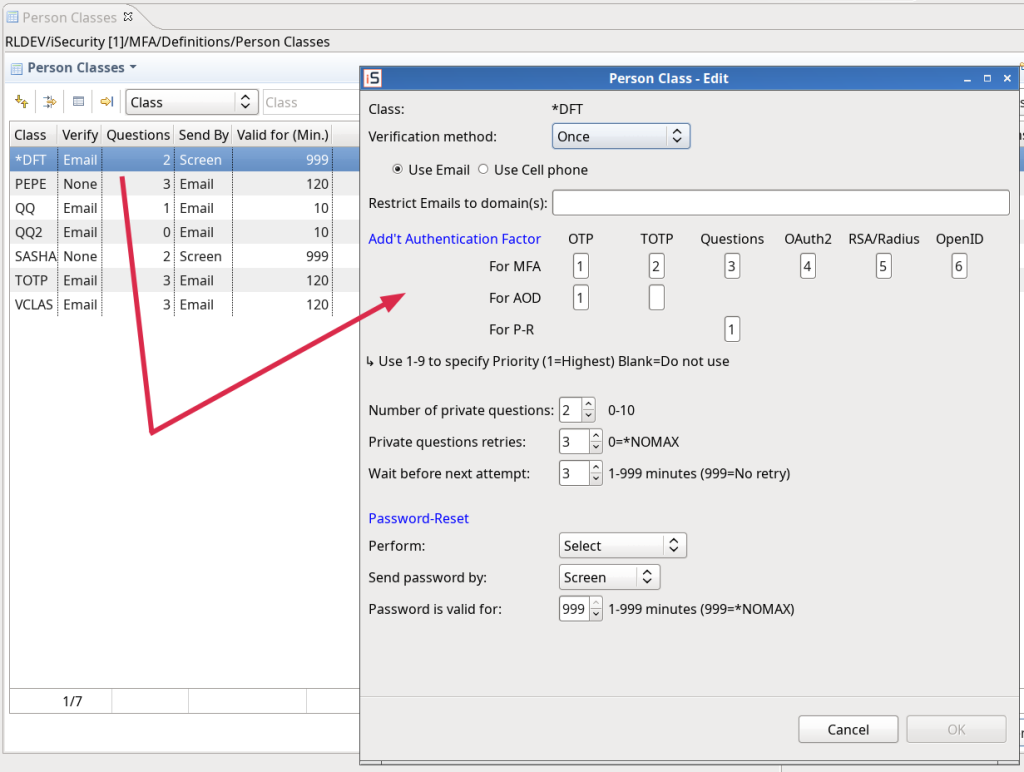
Add/Edit PrClass Dialog – adjustment to native
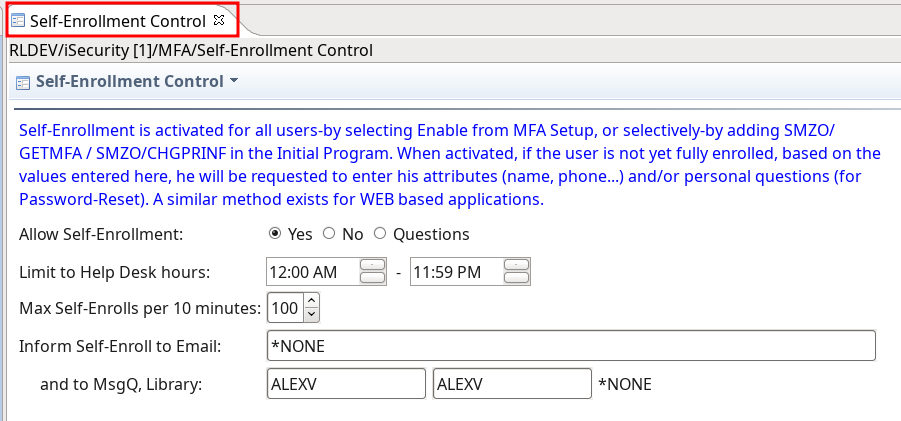
Added self enrollment
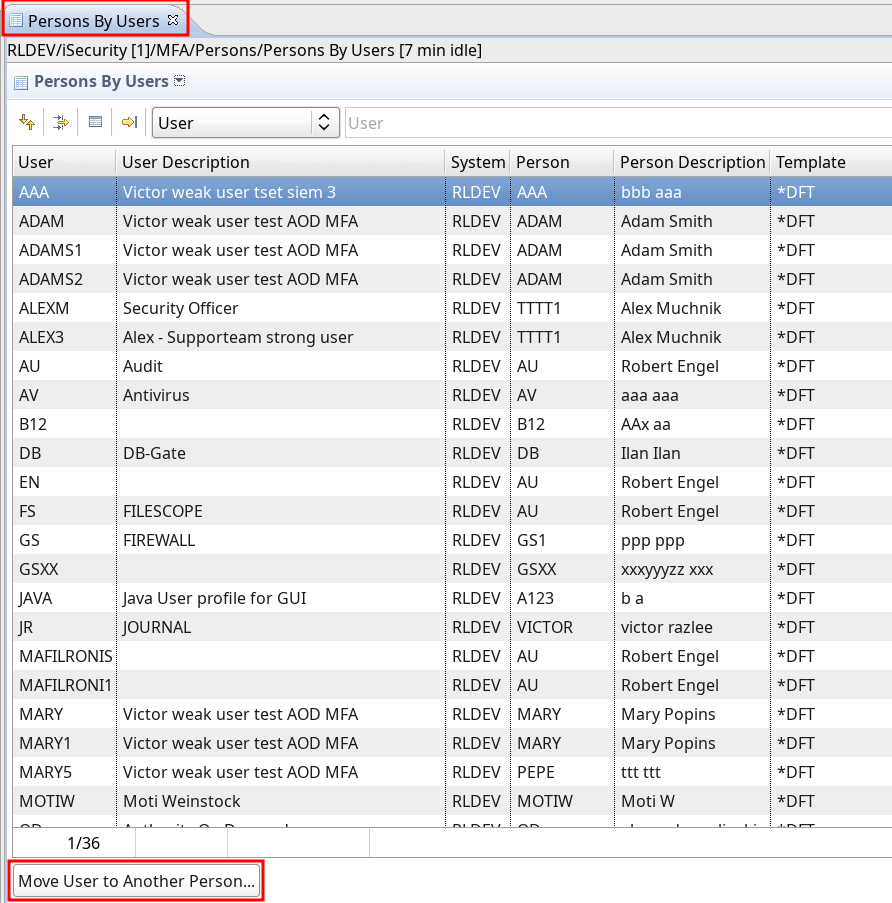
Added ‘Persons by Users’
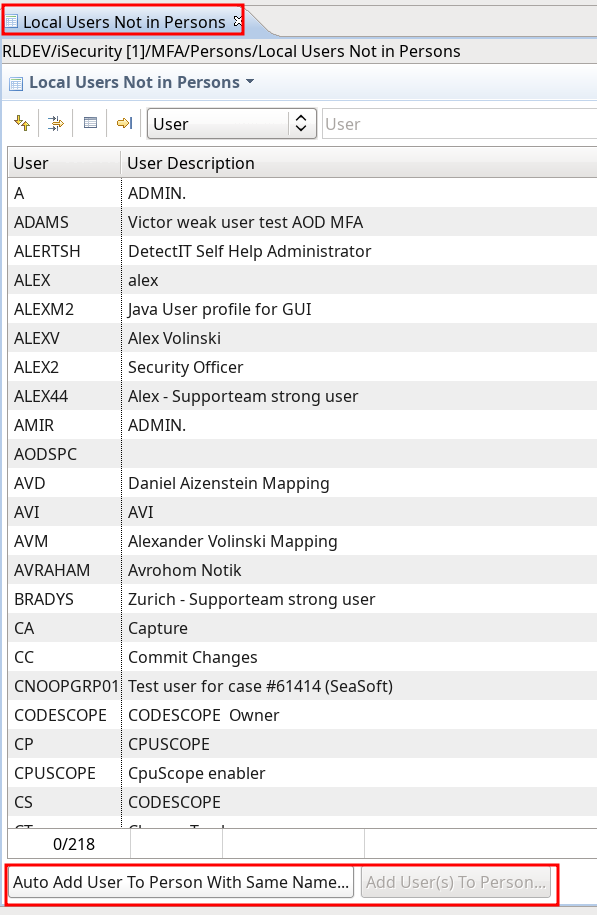
Added ‘Local users not in Person’
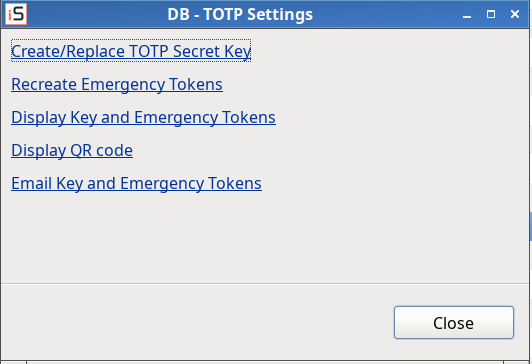
MFA – Persons: bug fix in delete a person – the systems of the person are also deleted now
Added External Authorization Providers:
Journal
Application Output – Operations adjusted to native
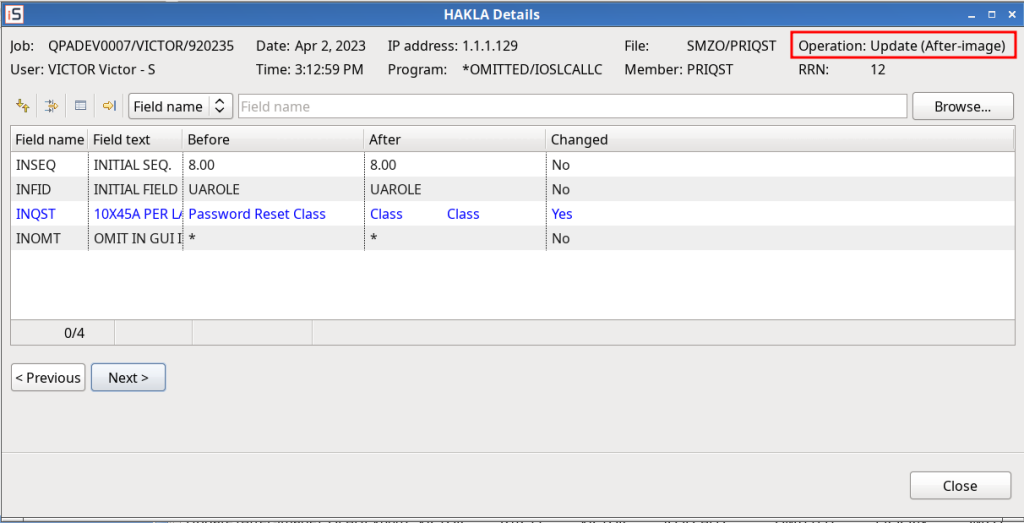
- General: Authorization program SMZ4/GSEPWDR is used now solely instead of it’s different copies on other libraries.
- MFA: First release.
- User Management: Change User Profile: Added a native command that supports long user profile passwords If QPWDLVL of the system is greater than ‘1’.
- Antivirus: General Definitions updated for 7.67:
- Antivirus/Anti-Ransomware native log: AV/AR native log:
- Firewall: Users and Groups: SSHD settings in place of Original Data Queue Server (ORDTAQ):
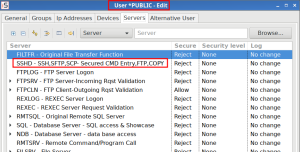
- Dashboard: Added systems table:
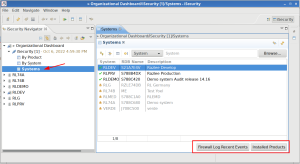
- A minor fix to setting up the product’s language at application start. At rare times, it was possible that Eclipse’s preference store was not yet available so we now use the default language, English.
Added a menu item to display information about offline updates
A window opens, displaying the manual for that operation, from which you can copy the link to the archived site.
- STRSEC implamantation with filtering and language selection
- Ready Reports: a correction to the way the time filter is set. In general:
* Last 1 day retrieves data for today from midnight to the last second of today
* Last x days retrieves data from (x-1) days ago at midnight to the last second of today - Run Query Wizard: removed links to old ready reports screens:
- Updated German translation
- System information about products: added export to HTML
- Firewall: native and IFS objects – user authorities – incorporate option (added in Firewall 8.26), S=Skip, to check and allow without logging
- Firewall: Work with IASP/generic* Lib Names: adjusted to native by adding IASP information
- PGP Encryption module: first release:
- Firewall – added ‘Incoming/Outgoing Socket Connections’. Node is displayed if Firewall version is higher than 18.27
- Dashboard – By Product – added export to HTML
- Dashboard – By System – added export to HTML
- For customers who still use Java6, the ‘Field Discovery’ node in Encryption is no longer displayed.
- Firewall Log – export to CSV: the length of the log record has been adjusted to the native value.
Firewall
- IFS Rule Wizard: a minor bug fix that goes along with a native PTF of SMZ8/CPRIFSSEC. Bug was encountered while displaying Firewall log and trying to modify rule for *FILSRV entries whose file system value contains spaces.
Encryption
- Field Discovery: HTML report as an alternative to reporting in the GUI
Anti-Virus
- Files to exclude updated to call a dedicated native program after each modification of the settings. A native PTF is needed for proper function.
Anti-Virus
- Excludes in real time and batch by regular expression adjusted to native.
- Added Excludes by generic names.
Anti-Ransomware
Files to Exclude: adjusted to native.
Anti-Ransomware
Added Inclusion/Exclusion screen
- Anti-Ransomware
Recycle Bin table and settings
- Work with detected attacks – bug fix for “Delete active attack”
- Run Audit/Firewall Queries
- Updated to support executing on multi-systems. When the “Select from list” button is selected the “Browse” button becomes enabled
- Clicking the “Browse” button displays a list of systems and system groups
Visualizer
Added “Select All” and “Deselect All” to popup menu of results panel
Firewall
User Security – added group indicator column to table and a button to list members of system groups
Anti Virus
Adjusted to native changes. New nodes: Scan STMF, Log
Activation: added status and Exit Programs status.
Anti Ransomware
First release
Object Integrity
Encryption
Field Discovery with Visualizer output
Analyze results in Visualizer
Dashboard
A new central account that is meant just for the dashboard. This empty account is added automatically by the GUI and user will point it to the organization’s central system.
Listing of products in multiple systems
Regular accounts will list just products per connected system
Journal
- Application definitions: adjusted to native changes as per SIEM (sending to SIEM1, SIEM2, SIEM3).
Audit
- Real Time Detection: Firewall rules are now fetched by the Firewall product. All the rest are fetched by the Audit product.
AntiVirus
- The node is added to the tree only if system is v7+
- Other enhancements to correspond to adjustments within IBM i programs.
Ready Reports Index
- ‘Query Type’ column is now called ‘Information Source’ and displays the query description.
- Product column displays the product name instead of the short name.
General
- Bug fix: In some table editors which are displaying tree structure, the “Expand All” button was missing
- Firewall – Users Wizard: adjustments to native changes by adding support for DBOPEN. Requires a native PTF.
- Spanish translation updated.
- New Dashboard screens – listing of products by system and by products
The Dashboard includes authorization checks and warnings, size checks, in-product active debug, and other useful features.
- Firewall Queries:
- Bug fix: when adding a query for a specific server, the wizard claimed that ‘Server is required’ even though the server existed.
- Added support for entry type ’50’ (*DBSTT Database statistic).
- Ready Reports: only the Reports Index node is displayed.
- Enhancements to Capture 5250 capture data.
- Send session by mail: grab session data even if it is in backup library.
- Applications Table: bug fix for error encountered just after adding a new Application or Report (NullPointerException).
- Activation and Application Status dialog: ZJOURNAL subsystem is now running in SMZTMPC instead of SMZJDTA. Both libraries are examined from now on.
- References to the file AU141TP refer to the file in SMZ4, even if it exists in SMZ8 . The file in SMZ4 is used instead.
- When running in Linux the reports are opened using Linux native tool (xdg-open).
- When running in Docker container (GUI via browser) all reports are converted to HTML and displayed in browser.
- Capture 5250, data: the calculation of the estimated number of frames for a session has been adjusted to be more accurate.
Updated Japanese and German translations. Implemented the following new Anti-Virus and ATP screens within the GUI for OS versions 7.1 and higher: Advanced Threat Protection/Real-Time Activities Setting Alerting General Definitions Maintenance/Start a New Log file Real-Time (“on access”) Real-Time Detection (“on access”)/Activation Real-Time Detection (“on access”)/Exclude Directories Real-Time Detection (“on access”)/Include Directories Refresh Virus Definitions/Display Last Update Time Refresh Virus Definitions/Refresh Refresh Virus Definitions/Schedule Refresh Scan IFS Directory (SCANAV Command)/Exclude on Regular Scan Scan IFS Directory (SCANAV Command)/Include on Regular Scan Scan IFS Directory (SCANAV Command)/Schedule Scan
Firewall – exit points:
- List adjusted to native with SSHD, PWDVL2 Password Dictionary and Sockets.
- Added “Check Free Style rules” to table and in the editing window
Change Tracker:
- Corrected the offset in the buffer returns from calling authorization program SMZT/GSEPWDR.
- Added support for auth level 3.
Audit & Firewall Queries:
when running a query to Visualizer output, it is possible now to drill directly into the underlying Firewall or Audit log. Status reports are not part of the feature as there is only the outfile behind them. Example with Firewall query. First step – run the query into Visualizer
Visualizer
In the case of a missing translated string, the string will be retrieved from the default English translation file. HTML Report:
- String externalization and additional German translation.
- Updated logo.
- Added a Graphics header which collapses and expands the chart.
Forcing GUI to work in SSL mode
By option 89, 59, you may specify:
GUI must run in SSL . . . Y Y=Yes.
GUI will stop working unless in SSL.
Visualizer for Firewall & Audit: new layout for time filter
Firewall – Server Settings: About server screen
Firewall RECALC: adjustment to native to support *DIFFONLY and *SAMEONLY. (this will function only for future Firewall release)
Firewall – incoming IP: added capability to specify generic* *LCL-XXXXXXXX names instead of IP
Firewall – General Parameters: Setting DB-OPEN and SQL adjusted to native. We support also ‘Files to Exclude’
Firewall: added Activation screen that includes Suspend/Resume Activity
Journal – Application Output
- Added a Type column to distinguish between Applications and Reports
- The title of the wizard window says if this is an Application or a Report.
- If report, the wizard is opened directly on the Time and Date page
Actions – Alert Messages: adjustment to native, SYSLOG is made into SIEM and address is enabled for writing for all types
AOD Activation: until version 5.00 the subsystem was SMZODTA/ZAUTH. Newer versions use SMZTMPC/ZAUTH.
Compliance – System Values Ranking – Tooltip displaying system value information
Compliance Plans: new Query name field is read only now and there is a new ‘Clear’ button
Compliance: setting of base line has been moved from Audit Settings to a new node under the Compliance node.
Added a new feature: Base-Line set as per Counts in Compliance Query. This will show only for Audit release greater than 13.46
New Replication node added to the root of the navigator tree and System Values Replication log has been moved there
Firewall, Server Settings: adjustment to native changes for 17.52 – SMZ8/GSEPNTR has one additional parameter.
Audit – Control Message Queues: adjusted to native (support for QHST)
Firewall (native version required is 17.52):
- Added ‘Check Firewall Security’.
- Firewall Log: added recalc feature.
Audit Queries: added action field as adjustment to native.
Audit General Groups: Item length can be 20 now and can contain any character.
Maintenance –
- AOD – added collected data.
- Change Tracker: added ‘Maintain CT Log Files’.
Journal Application – Visualizer tab: the command prompter is used for collecting latest data. This enables a recreate of the statistical file.
Journal: added activation screen.
AOD: Pin Code field was removed from wizard page
Compliance Queries – a fix for cases where Firewall is not installed on the AS400 .
Compliance queries have references to SMZTMPA that are checked now. Also there is a UI fix: upon editing a Compliance query, Firewall query radio button will be kept disabled
Compliance – a fix for listing $T and $S Audit queries when ‘Topic of values’ is selected. The fix is by proper CCSID handling.
- Capture 5250: Fix the problem of Capture displaying wrong screens.
- Compliance – displaying of screens data: a bug fix to prevent “SQL Exception: An undefined column name was detected” due to field name SVV#IT. (related to #20180055)
Capture 5250: Capture Data – all buttons controlling frames navigation are disabled upon data retrieval. When in slide show only the Play/Stop button is enabled.
This is a bug fix. In previous state when navigation buttons were pressed during data retrieval it resulted in displaying the wrong frames (the meta data of the frame showing on the frames combo did not match the frame).
As per customer request we bring back the ‘Export to Excel’ feature of the results table
The structure of the Compliance Node was updated
The Central Administration was adjusted to native
AP‐Journal
- Output Fields per File > Fields to ignore – a bug fix where in cases where there was a single field, it was presented as a Not Checked field.
Capture 5250
- Adjustment was made to the native (“green”) program.
When the screens are compressed, a call was added to the native program to make them available. - Also, a test was added for existence of member to enable more accurate message when screens are not found.
Authority on Demand (AOD)
- Active jobs – Node is properly assigned now to Authority on Demand™ (AOD).
Scheduler for Firewall/Audit/AP‐Journal
- Bug fix regarding the synchronization between the GUI and IBM’s prompter.
User input was saved incorrectly.
Authorization
- Bug fix regarding authority of the Change‐Tracker module – If library
SMZTwas missing, Anti‐Virus module’s menu option did not show on the iSecurity™ Navigator Window’s Menu tree.
Audit Real Time Detection Rules and Queries and Reports
- A warning message for empty filter, in Audit (and other applications) Queries and
Reports and was added.
For computability reasons (with the native/”green” version), two (2) changes were
made to the iSecurity™ Navigator Window:
- In the Authority on Demand (AOD) menu item, and
- In the Queries and Reports menu item.
Authority on Demand (AOD)
Instead of the old Authority on Demand Log menu item, now there is a Log menu item which presents three (3) sub‐menu items
Queries and Reports
In the Queries and Reports menu item, under the Queries sub‐menu item, an Authority on Demand Queries was added
In the Visualizer Business Intelligence products, both Audit and Firewall (and other applications as well), instead of the old Tab management system, now there is a new button ( > ) in the Tools Menu.
When clicked upon, it opens a drop‐down list box allowing selection of the Active Tab.
To save time on searching for the specific Tab name:
Once in the list box’s search bar (marked with yellow in the screen capture below), the user may type the letters included in the required Tab Name.
Scheduler
- The default for command output was adjusted to native.
Journal Application Definitions
- Adjusted to native with support for IASP, Auto Backup older data and Exit program (after filter).
- Added verification of journal when editing an application or a report.
User profile Report in Visualizer Business Intelligence
- ● Drill‐down feature extended to support:
$A, $B, $C, $D, $G, $P, $Qqueries types.
Compliance – Run Plan
- Adjustment to native changes.
The Excel output file was created with a name other than GUI requested.
Online Help
- Updated to display GUI only specific content.
Visualizer
- The constant String
**No value**is displayed now as'-'
Session Properties
- Session Properties now includes a list of installed modules, found in the Versions tab.
- In Scheduler for Audit, Firewall and AP‐Journal, the list of commands for a report
was adjusted to native.
AP‐Journal
- A new ‘Type’ column has been added to the Report/Application definitions, in the Application definition tree.
Editing Report or Application Definitions
NOTE: This can be done with Report/Application definitions that are not enabled.
- The AP‐Journal can now be modified, while the user can switch between the two ‘Types’
- When editing a file that belongs to a Report, only the Filters dialogue box is available
- When editing a file that belongs to an Application, only the filter and alerts are available
Application Output – Containers
Subsets which required the native command DSPAPJRN to be supplied as a PTF have been fixed.
Firewall Groups
A modification to enable work with large amount of users was added.
The Members table displays initially only included members.
The ‘Add’ button now prompts for multiple user additions.
By unchecking a checkbox, a user will be removed from the group.
Same table is available when editing all aspects of the group.