iSecurity SIEM & DAM Support
iSecurity SIEM & DAM Support works with every product that supports SYSLOG, like IBM’s Tivoli, McAfee, RSA enVision, Q1Labs, GFI Solutions, ArcSight, HPOpenView, CA UniCenter and others.
iSecurity supports Imperva SecureSphere DAM.
Integration with SIEM products for forensic analysis of security-related events is an increasingly important requirement at companies worldwide; indeed, Raz-Lee’s iSecurity suite has supported Syslog-to-SIEM for many years.
Key Features
Numerous iSecurity products integrate with SEM/SIEM systems by sending security alerts instantaneously to these systems.
Message alerts contain detailed event information about application data changes, deletes or reads of objects and files, emergency changes in user authorities, IFS viruses detected, malicious network access to the IBM i, and more.
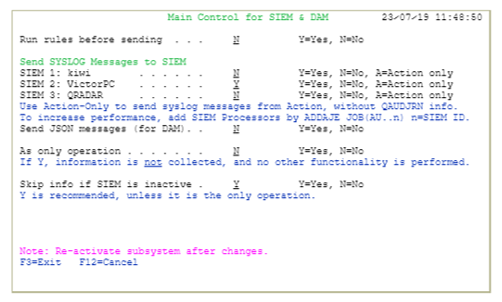
- Sends Syslog messages in parallel to up to 3 SIEM products.
- Transmission is supported via UDP, TCP or TLS (encrypted channel).
- Support in all iSecurity solutions enables infrastructure-related alerts and field-level application alerts on unauthorized data changes or access.
Syslog Self-Test facility runs on the IBM i, receiving messages locally for syslog message pre-check prior to sending to a remote server.
- Advanced filtering capabilities via specific severity code, part of the syslog standard, for each event/message and specifying the range of messages to send to each SIEM. This controls which messages will be sent to each SIEM.
- Advanced communications recovery features handle network problems or SIEM unavailability
- Enables sending extremely high volumes of information with virtually no performance impact.
Based on Clients Experience

Business Vertical: Finance & Banking.
Need: Compliance Cyber Security Regulations for Financial Entities.
“Being able to audit in real time is a great advantage, as every system in the company is secured and we have a global vision of our Cyber security.
The information also is passed to the SIEMs. The LOG records are available for BI afterwards.”
Request Demo
Please fill the following Form, our Sales Representatives will contact you as soon as possible.
