Ransomware attacks increased by over 37% in 2023 compared to the previous year, with the average enterprise ransom payment exceeding $100,000, with a $5.3 million average demand.
The most common targets were businesses in the manufacturing, services, and construction sectors. Ransomware attacks are becoming increasingly sophisticated, with attackers using a variety of techniques to exploit vulnerabilities in organizations’ systems and networks. These techniques include phishing, social engineering, and exploiting known vulnerabilities.
Ransomware attack trends
This year saw a staggering 550% surge in double extortion attacks on household and personal products, in addition to a significant 433.33% increase in attacks on the arts, entertainment, and recreation industry. It’s important to note that these sectors started from a relatively low baseline of attacks in the previous year’s report, making their growth appear more substantial.
These findings emphasize the pervasive and evolving nature of ransomware attacks targeting a wide range of industries. Even
sectors with historically low attack rates can experience sudden surges in ransomware incidents. The exponential growth in attacks reflects the increasing sophistication and relentless pursuit of profit by ransomware groups.
While the provided data focuses on the percentage change in extortion attacks by ransomware groups, it’s important to remember that it represents a specific aspect of the overall threat landscape. Many attacks may go unreported or undetected, making it challenging to capture the full scope of the problem.
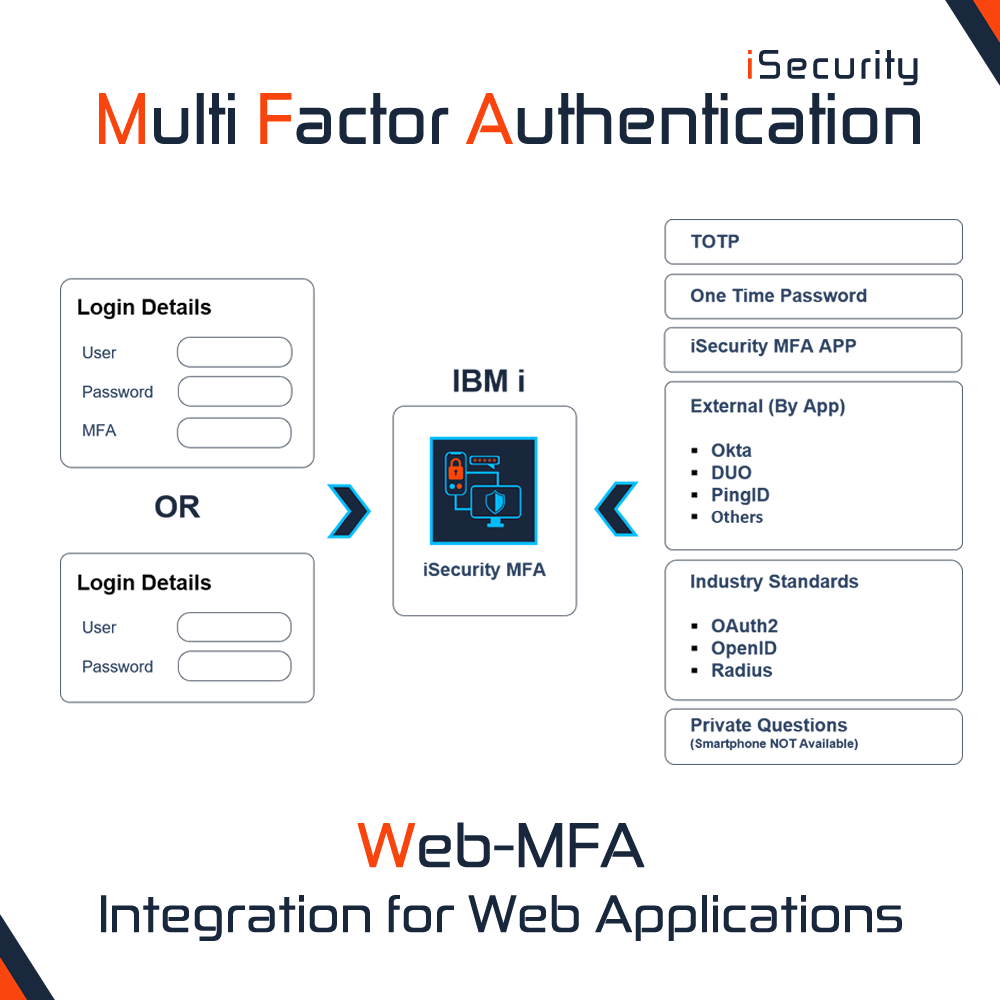
Ransomware victims by country
Ransomware groups target organizations from different industries and countries. The United States is the most
affected country, with 40.34% of overall victims impacted by double extortion attacks, followed by Canada (6.75%),
the United Kingdom (6.44%), Germany (4.92%), and France (3.89%).
2024 predictions
- Encryptionless ransom attacks: Traditional ransomware encrypts a victim’s files and demands a ransom for their release.
However, more and more cybercriminals are shifting toward encryptionless ransom attacks, which focus on stealing and
threatening to expose sensitive data instead of encrypting it. This approach adds a new layer of complexity and challenges for cybersecurity professionals. - AI-powered ransomware attacks: Ransomware groups are expected to increasingly leverage artificial intelligence (AI) capabilities—including chatbots, AI-developed malware code, machine learning algorithms, automated processes, and more—which will enable them to develop more sophisticated and efficient techniques, making it harder for traditional cybersecurity measures to detect and prevent such attacks. AI is also likely to lower the bar for developing ransomware by less sophisticated threat actors.
- Increased targeting of the cyber-insured: Cybercriminals have been focusing more on targeting organizations with cyber
insurance coverage, a profitable trend likely to continue to increase in the next year. Attackers know that insured victims
are more likely to pay ransoms since they can rely on the insurance to cover the costs. This targeting strategy aims to
maximize the chances of successful ransom payments. - Increased targeting of public entities: Another trend that ramped up in 2023 and is expected to continue is ransomware
attacks targeting cities, states, municipalities, law enforcement, K-12 schools, and other educational institutions and public entities. These entities often have a very low security posture to protect critical data and systems, making them attractive targets for cybercriminals seeking easy payouts or valuable, easily sold information. These types of attacks often significantly disrupt important public services and expose large caches of sensitiveinformation, including PII, financial data, private records, and much more. - New ransomware-as-a-service (RaaS) offerings: RaaS is a business model in which cybercriminals commission affiliates
to compromise organizations and deploy their ransomware. The vast majority of ransomware groups employ RaaS, and it
has proven effective over the years, leading to increases in the number of attacks each year. - Initial access brokers: There has been an increase in the number of threat groups that will breach an organization, and then sell access to a ransomware group (or affiliates of a ransomware group). This enables threat actors with penetration testing skills to profit from their work without having the expertise required to conduct a full-scale ransomware and/or encryptionless extortion attack.
- Attacks on cloud services: With the growing adoption of cloud computing and storage, ransomware attackers are likely to
develop new types of ransomware and campaigns optimized for targeting cloud services and workflows. Compromising
cloud environments can result in widespread damage, business disruption, and theft of sensitive data, impacting multiple users or organizations simultaneously. This possibility highlights the need for robust security measures and proactive defenses in cloud-based environments. - Attacks against additional operating systems and platforms: Ransomware groups will continue to expand their arsenals to attack mission-critical servers that run on non-Windows-based platforms. Threat actors have increasingly built ransomware to encrypt files on Linux and ESXi servers, which often host databases, file servers, and web servers. Some threat groups have also shown interest in developing ransomware for macOS.