Zero Trust has become one of cybersecurity’s most used buzzwords.
“never trust, always verify”
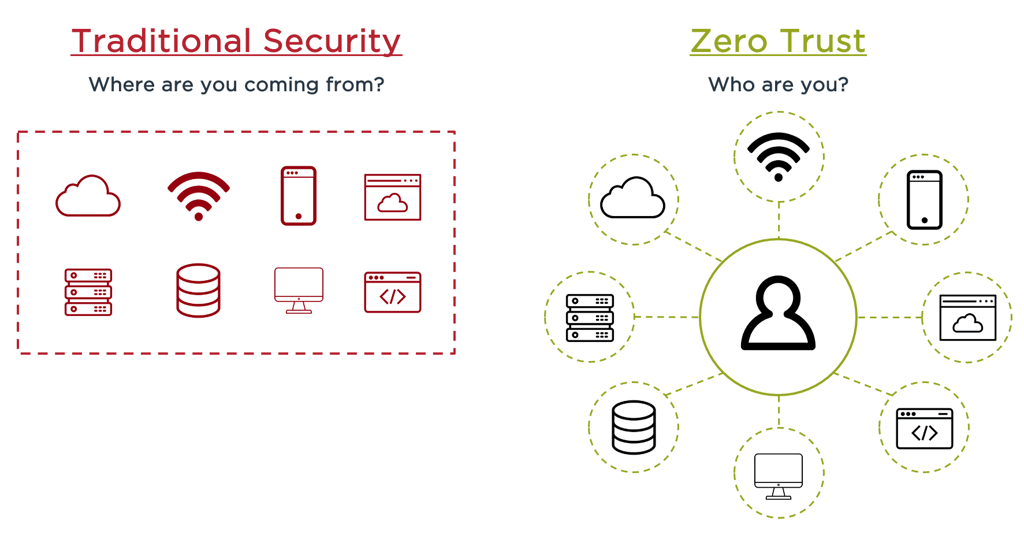
Zero Trust was created based on the realization that traditional security models operate on the outdated assumption that everything inside an organization’s network should be implicitly trusted.
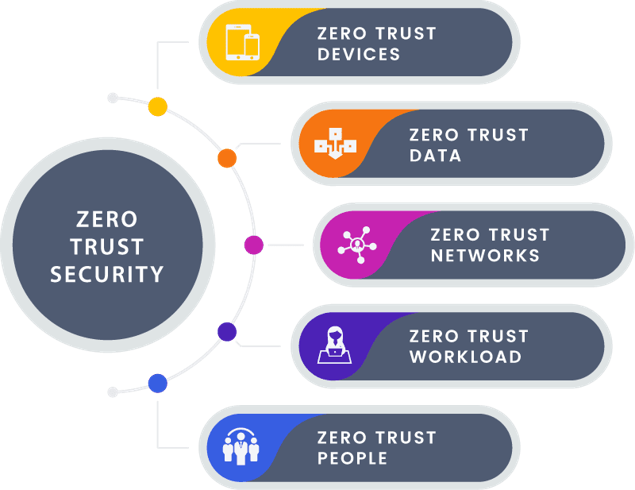
Zero Trust Devices
Addresses the need to isolate, secure and control all network-connected-devices, which have proliferated with the ascend of mobility and the use of Internet, creating an enormous vulnerability for attackers to exploit.
Zero Trust Data
Refers to methodologies for classifying and categorizing data, combined with technology solutions for securing and manage data including encryption of data in transit and at rest.
Zero Trust Networks
Refers to the ability to segment networks or isolate network assets and control communications among them. A critical issue in a Zero Trust approach.
Zero Trust Workload
Means securing the front-to-back application stacks that run critical business processes.
Zero Trust People
Encompasses strategies to limit and enforce users access, including technologies for authenticating users and continuously monitoring and governing their access privileges.
Traditional Security Vs Zero Trust
Firewall Protection
- Incoming and outgoing TCP/IP address filtering for Internet, FTP, REXEC, Telnet, and DHCP
- Subnet mask filtering
- Remote system (SNA) firewall protection for DDM, DRDA and Passthrough operations
- Powerful Intrusion Detection that enables Firewall to trigger proactive responses to the security administrator by MSGQ and email
- DHCP request packet validation
User Security
- User-to-server security for all server functions and exit points
- Prevents users from performing specific actions
- Verb support provides control over commands for specific servers
- Internal profile groups simplify rule creation for specific user groups
- DDM/DRDA security including pre- post- validation user swapping
- Protection over user sign-on from Telnet
- Limit user access to specific IPs and terminals
- Login control for FTP, REXEC, WSG and Pass-through
- User-definable exit program support (global and per server)
- User management and statistics tools ease system and security tasks
Object Security
- Controls object access at the level of specific action, such as read, write, delete, rename, and run
- Secures native O/S 400 and IFS objects
- Protects files, libraries, programs, commands, data queues and print files
- Definable rule exceptions for specific users


